Hack the Box Starting Point: Fawn Walkthrough

What is HackTheBox?
For those that may not already know, HacktheBox is a cyber range/ctf platform that allows you to practice those sweet sweet hacker skills on some vulnerable machines that our friends at HacktheBox host that we can connect to and pumble all for the sake of keeping us security professionals skills up to date.
Now with that being said there are two ways to connect to these HacktheBox machines (after you set up your account that is). One is via openvpn which you can download a key for and set all that up, I can show you on the next walkthrough, I’ll do it on a local VM. Or you can do what I’ll be doing for this walkthrough, you can use their pwnbox. It’s a Parrot OS VM you can spin up in your browser that you can use to dive right into attacking machines. Granted you only get two hours of access for a free account so you can either pay a monthly subscription or have a local VM to do all your exploitation with. Alright if you’re following along with me feel free to make an account and spin up your pwnbox and let’s tackle the Fawn machine.
Navigating to Starting Point

So after you make an account and login you’ll be presented with something like this for your homepage. Go ahead and click on Starting Point to… well… go to starting point.
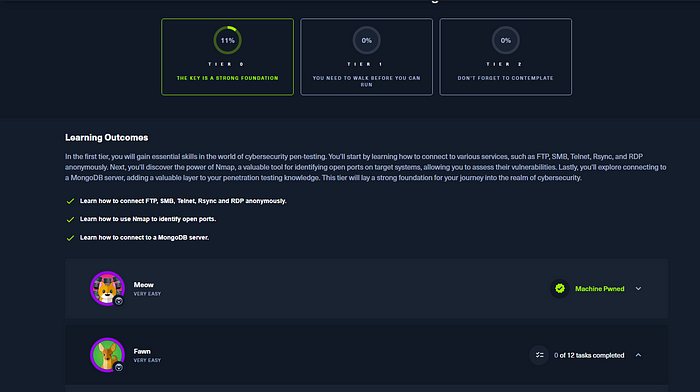
Here you can see some of the machines HacktheBox recommends we start off with. Now I have already “pwned” meow, hence why my walkthrough is starting with Fawn. Let’s click on Fawn.
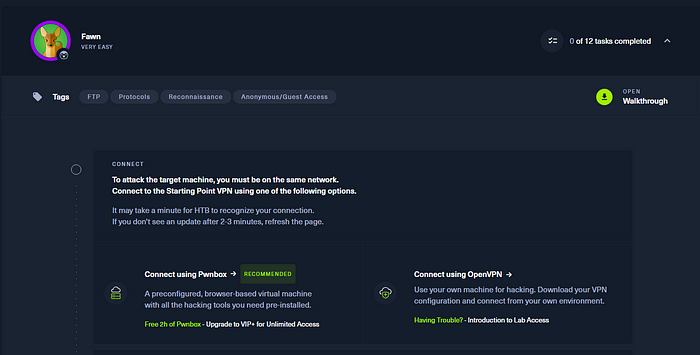
We see a few things. The name of the machine, it’s difficulty, how many objectives it takes to pwn this box, some tags of topics associated with this machine and a walkthrough button if you want a better written walkthrough. As I mentioned there are two ways to connect to the machines we see here, via pwnbox or downloading a OpenVPN config file.
For this walkthrough, we’ll be using our pwnbox instance to complete this machine, before that though let’s look at the objectives just to see what we’re in for.



Now let’s spawn our pwnbox so we can start answering these questions.

Here’s our pwnbox. Just for some background pwnbox, again, is a variation of the Parrot OS pentesting distribution similar to Kali Linux. It’s also a Debian based distro for those of you who didn’t know. Now let’s click on that Terminal icon on that top application bar and get our shell.
Perfect. Let’s ho back to Fawn and answer some questions. Hit the Spawn Machine button and wait for the vulnerable machine to spawn which might take a minute, feel free to get up and stretch or something while that’s happening.
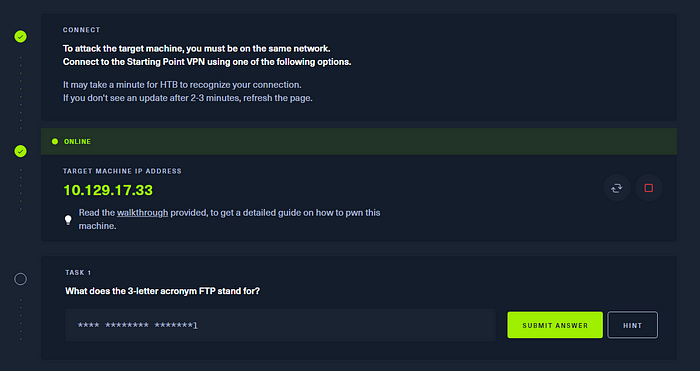
Alright, our instance has spawned and we get out first question. What does FTP stand for?
FTP or File Transfer Protocol is a pretty old protocol used for… file transfers, you guessed it. You can access a FTP server via the command line and issue commands to dowload and move around files remotely. The issue with FTP though is that it is an unencrypted protocol so if you ever see it in the wild that’s already a security concern as anyone able to access the network traffic can see everything happening including authentication (i.e. passwords).
So for this objective go ahead and enter file transfer protocol and let’s hit the next question.

FTP operates on two ports technically. The client (us reaching out to the FTP server) are going to use port 20, but the server itself listens for incoming connections on port… 21. So that’s our answer.

Now this one can actually be a little tricky because there’s two answers. We can see however the asnwer they’re looking for ends with p so that narrows down the choices. However, for your situational awareness, there are indeed two FTP protocols with security in place. There is FTPS and SFTP. What’s the difference? Well, SFTP is FTP tunneled via SSH via port 22 and SFTP add TLS encryption over the FTP protocol and is usually found on ports 989 and 990. The asnwer for this question though will be SFTP as I like to remember it Secure Shell FTP.

Now for those of you who have done any basic network troubleshooting you will recognize we need to use thing ping command so let’s go ahead and go to our shell and issue the command ping -c 4 [target ip] .
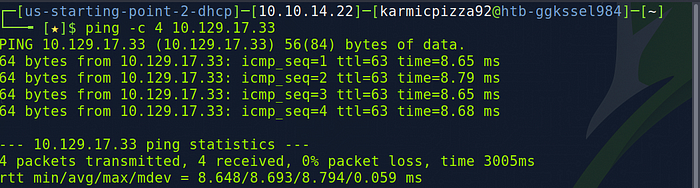
By doing this we ensure that we can connect to the target and that the target is alive and kicking. The -c 4 was just to limit the number of ICMP echo requests (pings) to 4 so that way in doesn’t go on forever. Anyways the answer to our question here is going to be ping.

Alright time to introduce our first tool, nmap. Nmap is a powerful network scanning tool used by lots of IT folk for various IT reasons although security experts also love it for pentration tests. It’s not only capable of scanning the network and seeing all the hosts, but it can also perform things like OS detection, version scanning and it has scripting capabilities. The question however is asking for us to do a version scan. However if we look at the next question

it is also asking us to find out the OS running on the target. So let’s do both at once. Go to your shell and enter:
sudo nmap -sV -O [target ip]
This may take a minute, so take a break from all this knowledge with a glass of water or something.
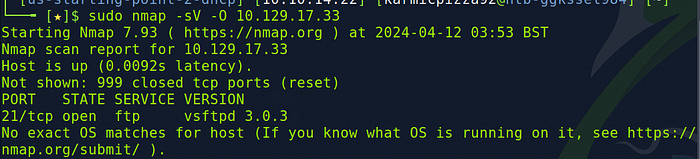
So I shaved off a little of the output so we can focus on the important stuff. We found the version of FTP running which is vsftpd 3.0.3.
However, the fingerprint from the OS detection matches too many signatures for Nmap to give a reliable answer. At the bottom of our nmap output though it shows us this.

Let’s try Unix as our answer.
Nice. As for the next question, a lot of Linux commands have a help option by issuing either the -h or — help option. Let’s try in this case to issue the FTP command with the -h option.
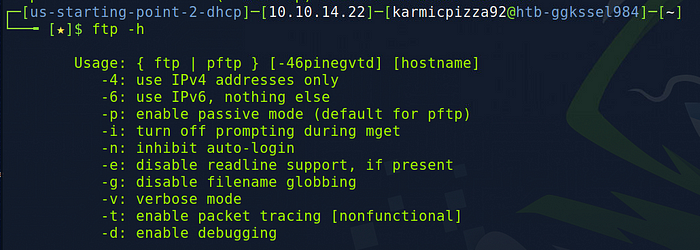

Alright onto the next question.

So FTP does allow unauthenticated connections with its default configuration (obviously not great). The account that allows this is the anonymous account which is our answer.
Alright let’s try to FTP into the server via the anonymous account. Let’s run the command
ftp [target ip]
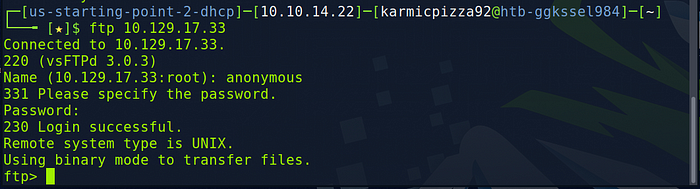
So we establish the connection to the server which asks us for a username. We provide the anonymous username and then it asks for a password. Typically with this type of account there isn’t a password so let’s hit enter. Then we see the login succesful message with the 230 code, which is our answer.
On linux, the way we can files on our current directory is with the ls command, let’s see if this works on our FTP server.
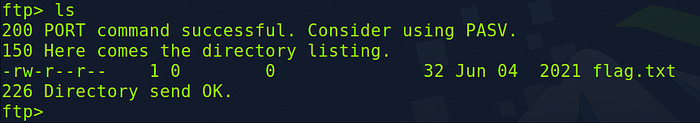
Let’s type ls now in the answer box and HacktheBox says that’s our answer.
Well off the top of my head, I’m not sure, let’s see if the FTP server can offer us any help.

By typing help and hitting enter we get a lot of useful commands we can use. That get command looks promising let’s try that.
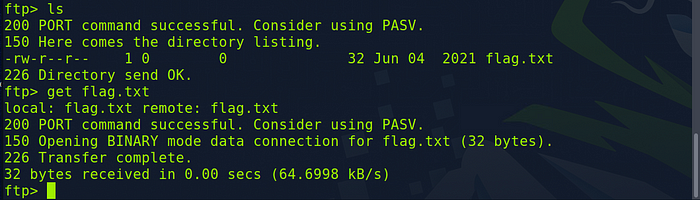
So I issue the ls command again to see the name of our file, flag.txt. Then I issue get flag.txt and we get a transfer complete. Before we look at that file let’s answer get to the question.

Last objective, we’re almost there guys. So that file we just downloaded? That probably has something to do with our answer here. Let’s exit the ftp connection by typing exit.

Now if we type ls on our machine we should see the file we downloaded from the ftp server.
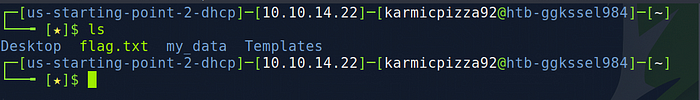
Awesome, we can use that cat command now to view the file contents.

Let’s copy and paste that into our answer box and………
Just like that. we’ve pwned our first (or second) machine on HacktheBox.
In Conclusion
I hope that I taught you something or gave you a decent refresher on some of this stuff. HacktheBox is great for developing practical cyber security skills and practicing what we’re all learning and that’s so so important in todays environment. Lot’s of people know the theory, but lack the practical knowledge to back it up and this is a great way to gain that. I hope to cover all of the starting point machines, so stay tuned for that. Please share and feel free to provide feedback and I hope to see you next time, thank you for reading!
